The following provides a detailed summary of wireless terms and acronyms and more in-depth explanations of the topic. It assumes little prior knowledge of wireless networking and is aimed at providing background for the terminology used in the NB9W Wireless Security screens.
Warning: Wireless Networking is a technically challenging subject!
The two major aims of wireless network security are:
(1) to prevent unauthorised persons from joining the network and
(2) to prevent interception of network data or ‘eavesdropping’. These aims are accomplished by:
· Authentication: establishes the identity of those seeking to join the network
· Encryption: ensures that data is protected in such a way that those outside the network cannot access it.
The term ‘network key’ is often used in the context of wireless networking. The Network Key can be a text string, although in some systems network keys are generated from a ‘pass-phrase’ which is entered in one field from which up to four keys are derived in fields underneath the entry field.
In all cases, the Wireless Router/Access Point and the workstations wishing to connect must use the same Network Key which needs to be communicated to clients prior to connection.
‘Re-keying’ refers to the frequency with which network keys are changed; for security purposes, they need to be changed frequently in case they re-occur frequently enough to identify them.
In some wireless systems, network keys are entered by a variety of means including:
ASCII – any letter, number, or punctuation mark but no special characters
Hex – Letters A-F, Numbers 0-9 only
Pass phrase – enter a phrase in the top field of a set of fields, an algorithm then generates a series of keys based on the entered values.
These methods have been standardised in the later implementations of Wireless Security and are easier to use in WPA.
‘WEP’ stands for Wireless Equivalent Privacy and was the original wireless security method. Over time it was found to be vulnerable to attacks based on de-coding the ‘keys’ used to encrypt the data. While no longer recommended for enterprise-level security, WEP is certainly secure from casual interception and will repel any non-specialised attempt to join the network or intercept data; it can be penetrated with various kinds of software tools and techniques but these are beyond the capability of the average computer user.
‘WPA’ stands for Wi-Fi Protected Access and is an improvement on WEP. WPA2 offers further refinements to WPA.
WPA and WPA2 both comprise a number of different wireless security elements and methods that can be adapted to a variety of situations depending on the requirements. A lot of what is provided is applicable to enterprise-level wireless networking, in other words, suitable for businesses who wish to deploy strict security methods and policies for their employees. Accordingly, these technologies will exceed the requirements of home users.
An important element of WPA security is a RADIUS server (stands for Remote Access Dial-in User Service). The RADIUS server typically sits in the server room of a business or department and authenticates and manages user requests for connection. Home users will generally never have to bother about RADIUS server details.
In nearly all cases, the default security method, which is WEP, or WPA-PSK will provide adequate security for home wireless networks.
Other wireless security elements shall be explained in context below.
Network Authentication specifies the type of network authentication. The default value is 'Open'.
Open: Under Open System authentication, any wireless station can request authentication.
Shared: Under Shared Key authentication, each wireless station is assumed to have received a secret shared key over a secure channel that is independent from the 802.11 wireless network communications channel (i.e. verbally). To use Shared Key authentication, you must have a network key assigned to the clients trying to connect to your NB9W.
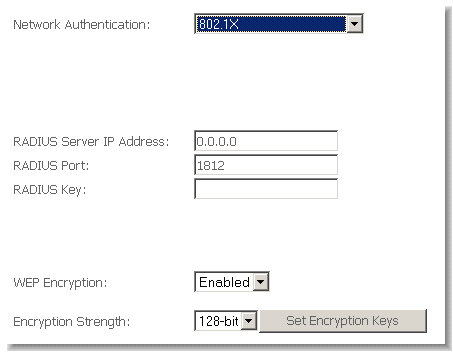
802.1X

802.1X security requires the presence of a RADIUS server, and specification of the IP address of a RADIUS server, the port on which to connect to it, and the Shared Key used to authenticate with it.
Disregard this security setting unless you are setting up or connecting to a RADIUS server.
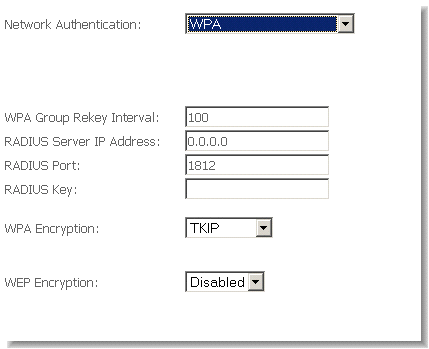
WPA also requires a RADIUS server to provide client authentication. 802.1X also requires specification of the 'WPA Group Rekey Interval' which is the rate that the RADIUS server sends a new Group Key out to all clients. The Re-Keying process is part of WPA's enhanced security. This method also requires specification of the IP address of a RADIUS server, the port on which to connect to the RADIUS server, and the shared key used to authenticate with the RADIUS server.
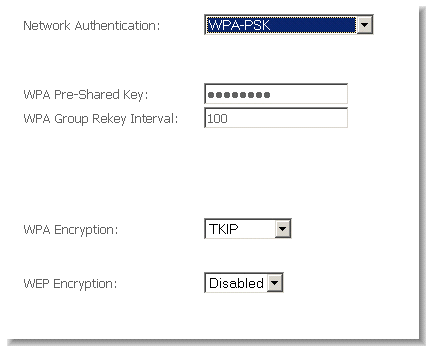
WPA-PSK is a special mode of WPA providing strong encryption without access to a RADIUS server.
In this mode encryption keys are automatically changed (rekeyed) and authentication re-established between devices after a specified period referred to as the 'WPA Group Rekey Interval'.
WPA-PSK is far superior to WEP and provides stronger protection for the home/SOHO user for two reasons: first, the process used to generate the encryption key is very rigorous and second, the rekeying (or key changing) is done very quickly. This stops even the most determined hacker from gathering enough data to identify the key and so break the encryption.
WEP is confusing because of the various types of ‘network keys’ vendors use (HEX, ASCII, or passphrase) and because home users mix and match equipment from multiple vendors, all using different types of keys. But WPA-PSK employs a consistent, easy to use method to secure your network. This method uses a passphrase (also called a shared secret) that must be entered in both the NB9W and the wireless clients. This shared secret can be between 8 and 63 characters and can include special characters and spaces. The 'WPA Pre-Shared Key' should be a random sequence of either keyboard characters (upper and lowercase letters, numbers, and punctuation) at least 20 characters long, or hexadecimal digits (numbers 0-9 and letters A-F) at least 24 hexadecimal digits long.
NOTE: The less obvious, longer and more ‘random’ your 'WPA Pre-Shared Key', the more secure your network.
Note the following 'WPA Encryption' options:
TKIP:
The Temporal Key Integrity Protocol (TKIP) takes over after the initial shared secret is entered in your wireless devices and handles the encryption and automatic rekeying.
AES:
WPA defines the use of Advanced Encryption Standard (AES) as an additional replacement for WEP encryption. Because you may not be able to add AES support through a firmware update to your existing wireless clients / equipment, support for AES is optional and is dependent on vendor driver support.
TKIP+AES:
This will allow either TKIP or AES wireless clients to connect to your NB9W.
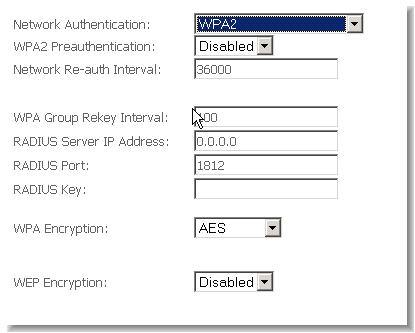
'WPA Pre-authentication' support in WPA2 allows a client to pre-authenticate with the NB9W toward which it is moving, while maintaining a connection to the access point it's moving away from. This new capability allows the roaming to occur in less than 1/10th of a second while a traditional roam without PMK caching and pre-authentication would take more than one second. Time-sensitive applications like Citrix, video, or VoIP will all break without fast roaming.
'Network Re-Auth Interval' is the interval specified (seconds) that the wireless client needs to re-authenticate with the NB9W.
For the remainder of the fields required, see above.
Same as WPA-PSK, but you can only use AES with WPA2 and not WPA.
Enables WPA2 or WPA wireless clients to connect to the NB9W. Requires a RADIUS server to authenticate the wireless clients.
Enables WPA2 and WPA clients to authenticate using a PSK (Pre-Shared Key) instead of a RADIUS server.